Rubrik and Pure Storage
Complete Cyber Resilience for Mission Critical Data
Secure data and minimize downtime with a cyber resilience stack that combines Pure FlashArray, Rubrik Security Cloud, and Pure FlashBlade.
Gain cyber resilience with a three-layered defense strategy
With the increasing risk of cyber threats and exponential growth of data comes the unprecedented challenge of securing it.
Rubrik and Pure Storage offer a complete cyber resilience solution architecture to deliver a modern, efficient, and secure approach to data protection across short-term and long-term storage needs.
Scalable and Cost-effective
Ensure critical data is secure and quickly recoverable with solid performance and cost management.
Advanced Threat Analytics
Continuously monitor data risks and threats for rapid identification and mitigation.
Defense in Depth
Maintain three copies of data stored on two media types, one off-site, one immutable, and with zero errors.
Rubrik + Pure Storage: The Math Behind the Cyber Resilience Stack
Traditional data protection solutions struggle to keep pace. See how Rubrik and Pure Storage have joined forces to deliver a 3-layered defense strategy to secure data and minimize downtime.
Keep data secure and available
Organization’s struggle to maintain data security and accessibility in the face of sophisticated cyber attacks.
Rubrik and Pure Storage bring together our industry leading technologies to create a multi-tiered defense strategy, ensuring critical data remains secure, immutable, and readily available when you need it most.
Immutable Snapshots
Store natively immutable copies immediately adjacent to production workloads with Pure FlashArray
Bucket level-immutability
Deliver indelible copies to prevent data alteration and deletion by bad actors with Pure FlashBlade
SafeMode Governance
Provide full privileged user attack protection for all data copies across the Pure Storage Platform
Rubrik Secure Vault
Harness air-gapped, immutable, access-controlled backups to recover when you need to most
Stay protected with automation
Manual data protection processes are time-consuming, error-prone, and often leave critical assets vulnerable.
Rubrik and Pure Storage's automated discovery and protection capabilities streamline your data security efforts, ensuring comprehensive coverage across your entire infrastructure without the need for constant manual intervention.
Default Protection Groups
Automatically protect new production workloads with indelible snapshots
Automated Discovery
Automatically discover data across physical systems, VMs, databases, and containers as it is created
Automated Protection
Replace thousands of backup jobs and automatically protect data with just a few inherited policies
Rubrik + Pure Storage: Cyber Resilience Stack
Discover how Rubrik and Pure Storage’s joint cyber resilience stack delivers unparalleled data protection and rapid recovery at scale.
Efficiently backup and recover
Traditional backup and recovery solutions often struggle with performance bottlenecks and lengthy recovery times, putting business continuity at risk.
By leveraging Pure Storage's flash-optimized performance and Rubrik's intelligent data management, organizations can achieve rapid backups and recoveries, minimizing downtime and data loss.
Scalability & Performance
Support the lowest possible RTO with performance-optimized recovery
Flash-Speed Backups
Minimize impact on production with rapid backups
Incremental Forever
Reduce local storage and improve backup times using change region tracking
Parallel Streaming
Scalability for the largest enterprises with rapid data ingest and flash performance
Enable cyber resilience
As cyber threats evolve, many organizations lack the visibility and tools needed to detect, respond to, and recover from attacks effectively.
Rubrik and Pure Storage's integrated cyber resilience features provide comprehensive threat detection, anomaly identification, and rapid recovery capabilities, empowering organizations to stay ahead of potential threats and quickly bounce back from incidents.
Cyber Recovery SLA
Get back in business as soon as possible with a clean recovery array and recovery plan
Cyber Resilience Assessment
Ensure all data is protected with best practices with full visibility into production workloads
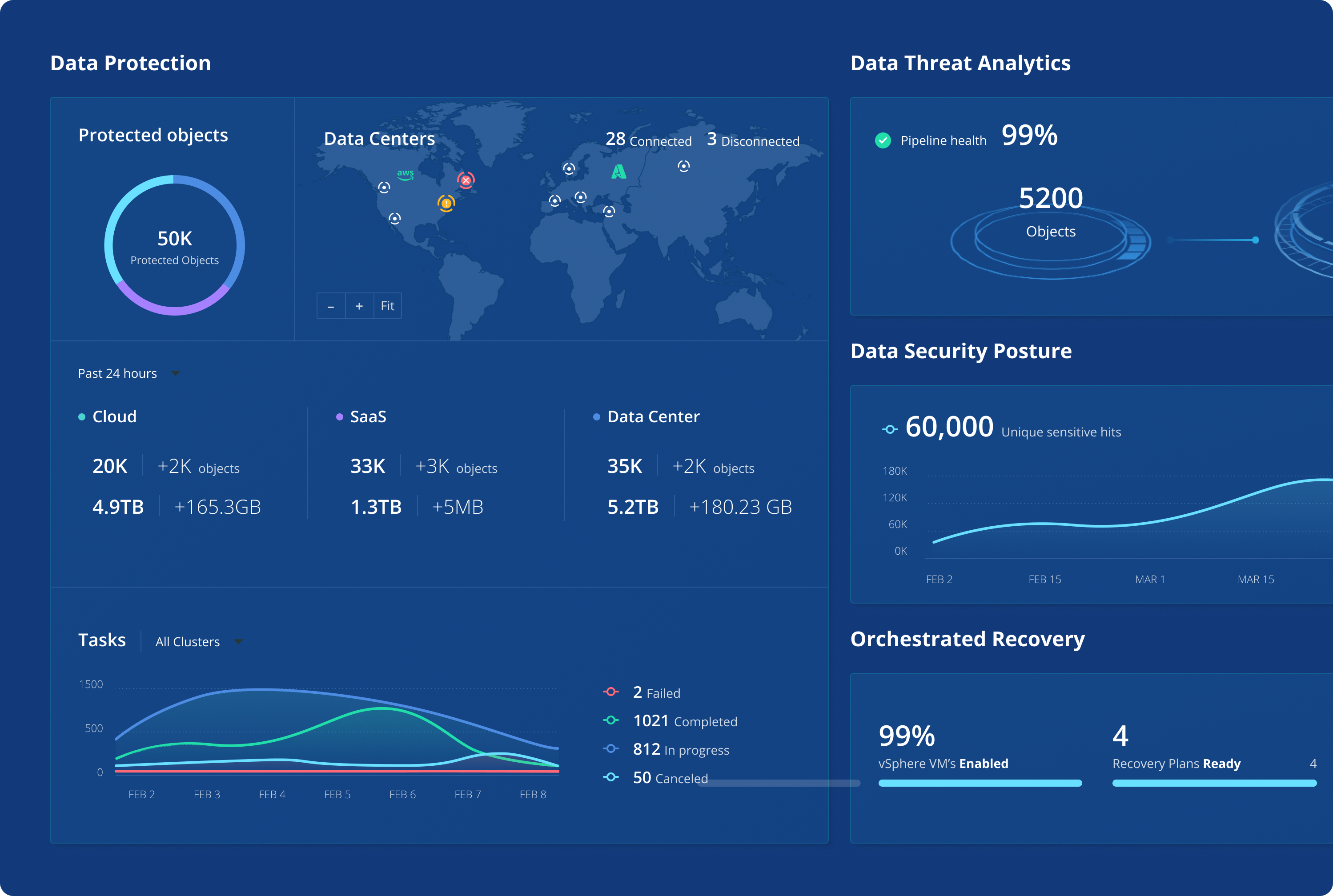
Data Threat Analytics
Continuously monitor for data threats, including ransomware and indicators of compromise
Data Security Posture
Identify and monitor sensitive data exposure with intelligent risk monitoring
Built for unstructured data at scale
Legacy storage and backup solutions can’t keep up with the explosive growth of unstructured data, leading to performance bottlenecks, operational complexity, and increased vulnerability to cyber threats.
Rubrik and Pure Storage provide an efficient, high-performance solution that scales effortlessly, eliminates bottlenecks, and strengthens cyber resilience—ensuring your unstructured data stays protected, accessible, and ready for the demands of modern workloads.
Performant Storage Built for Modern Unstructured Workloads
Ensure your file services can dynamically change and adapt in real time to meet the demands of modern applications.
Efficient and Secure Backup and Recovery at Scale
Secure unstructured data at petabyte scale with rapid and efficient backup and recovery from cyber attacks.
Rubrik & Pure Storage: Cyber Resilience Stack
Rubrik and Pure Storage® have joined forces to offer a complete cyber resilience stack that combines the strengths of Pure Storage FlashArrayTM, Rubrik Security Cloud, and Pure Storage FlashBlade® to secure data and minimize downtime.

Ransomware Recovery Warranty
Rubrik offers a $10M ransomware recovery warranty for Enterprise Edition and Enterprise Proactive Edition customers protecting their data on premises and in Rubrik managed cloud environments.
Ready to get started?
Get a personalized demo of the Rubrik Zero Trust Data Security platform.


