What is Rubrik?
Data Security and Zero Trust Explained
Rubrik is a cybersecurity company that focuses on much more than data backups. Learn how we implement Zero Trust Data Security to protect your data.
Cyber prevention alone is not enough
Cyberattacks are increasing in frequency and sophistication. Despite large investments in infrastructure security tools, bad actors are finding their way through to the data. And they know legacy backup tools are vulnerable, so they are increasingly targeting backup data.
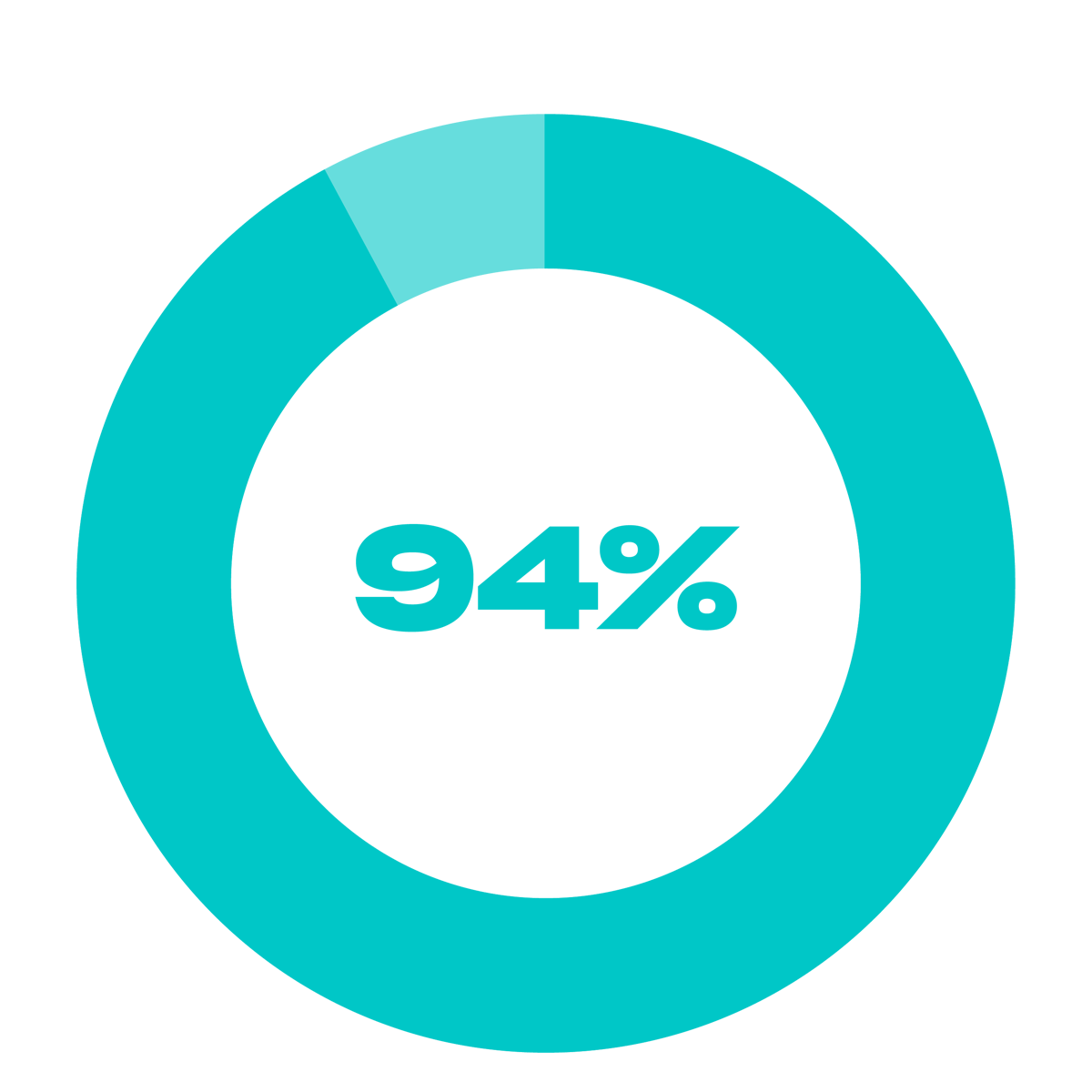
of IT and security leaders reported their organization experienced a significant cyberattack last year.
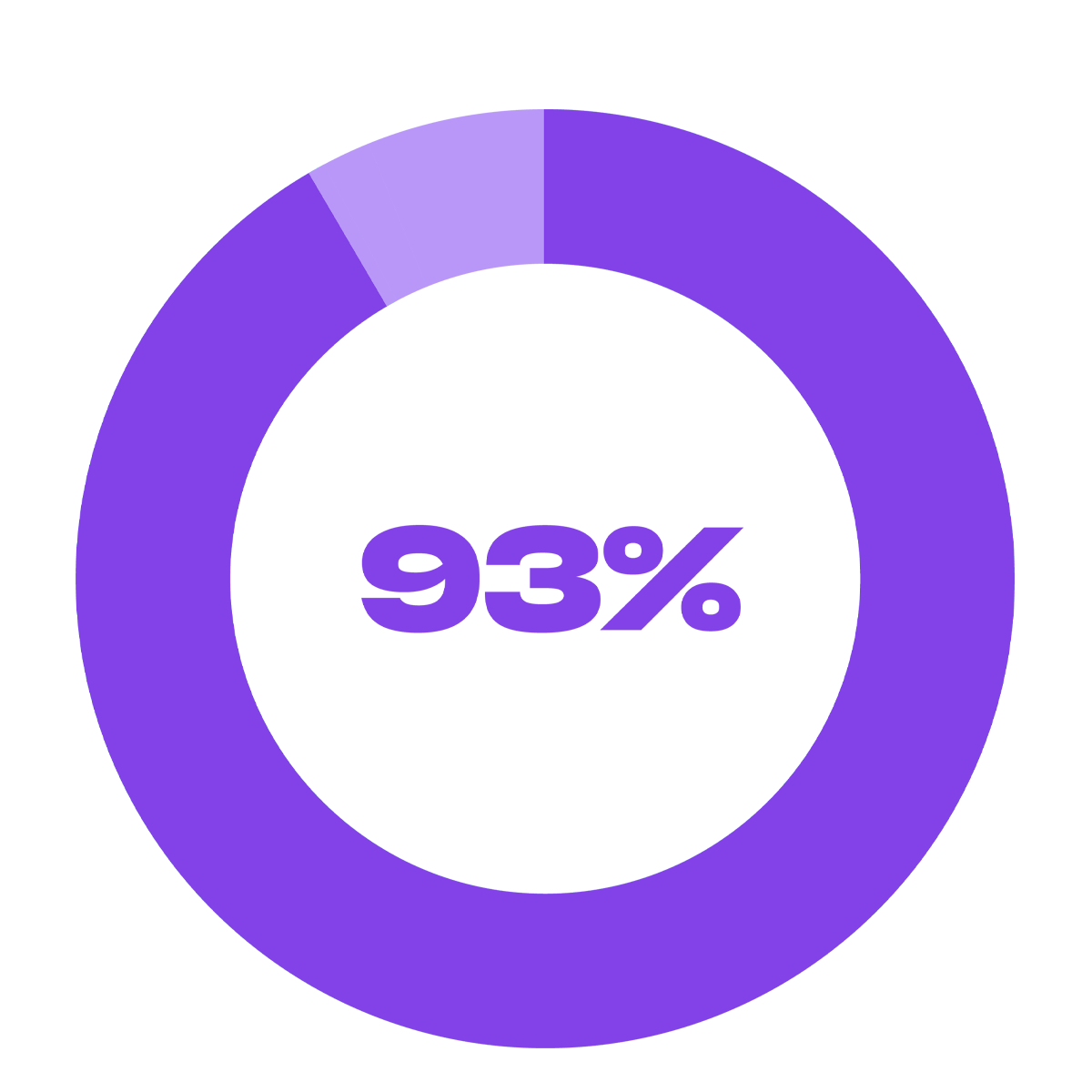
of external organizations conducted a formal data loss notification to a governing organization.
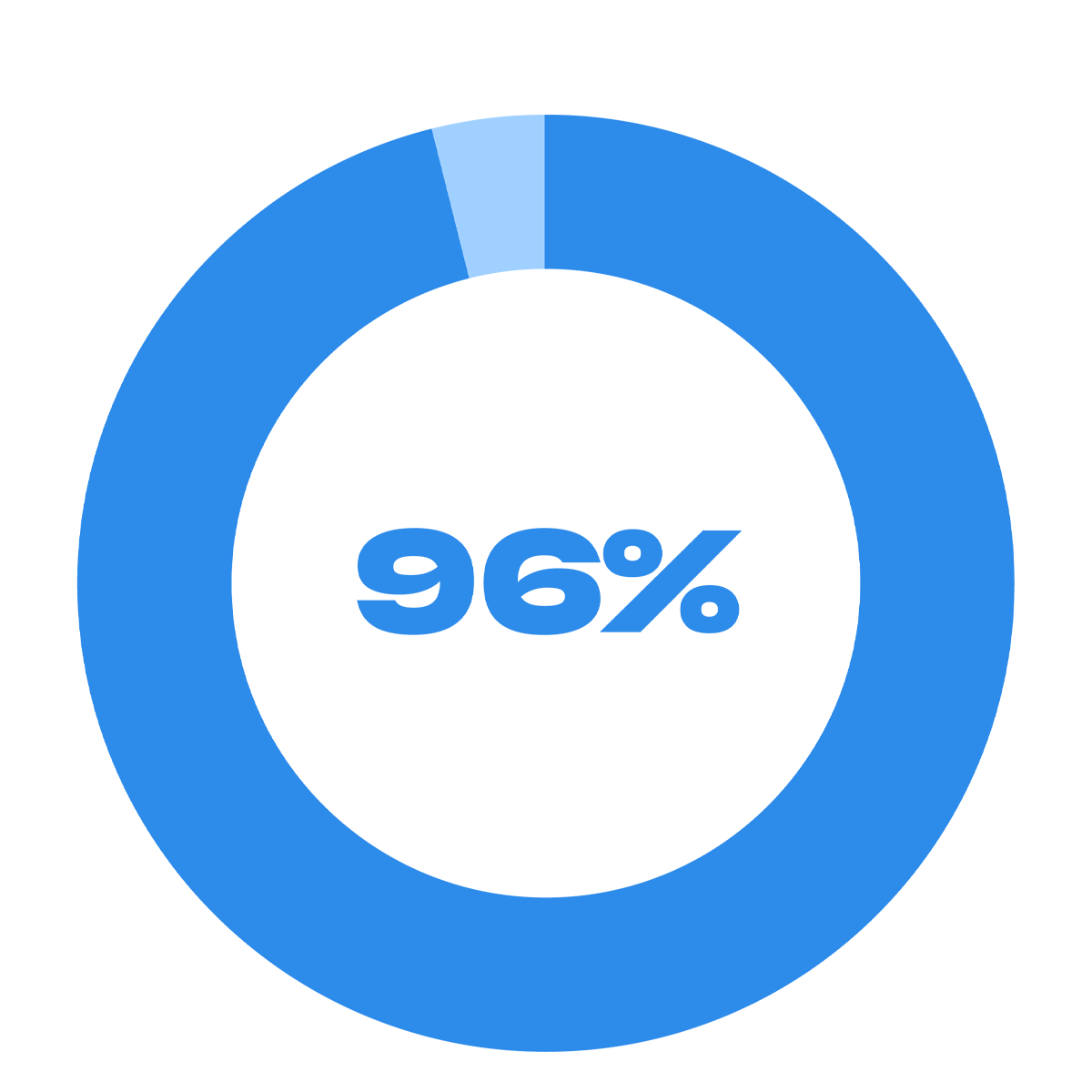
of attacks against external organizations where attackers tried to affect backups were at least partially successful.
When a cyber attack takes down your data, it takes down your organization. It’s time for a new approach–one that marries the investments you’ve made in infrastructure security with data security.
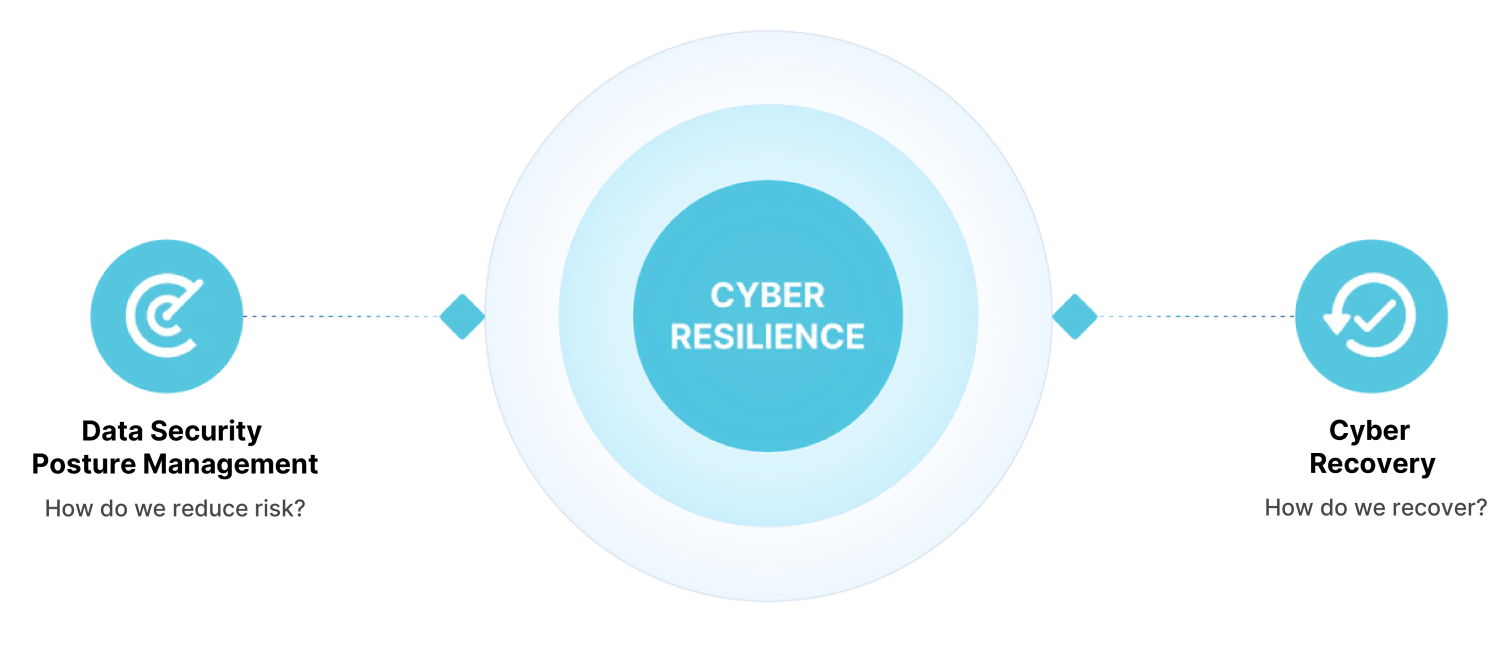
Make your organization cyber resilient
Cyber resilience enables organizations to:
Keep all your data safe and available
Spot data risks and threats sooner
Recover your data quickly, securely and confidently.
Gartner 2024 Critical Capabilities report for Enterprise Backup and Recovery Software Solutions
Rubrik ranks #1 in the Ransomware Protection, Detection, and Recovery Use Case!

Over 6,100 organizations trust Rubrik to keep their data secure
What is Rubrik Security Cloud?
Rubrik Security Cloud delivers complete cyber resilience for your data across enterprise, cloud, and SaaS.
.png)
Safeguard data with secure backups
Protect your data from insider threats or ransomware with air-gapped, immutable, access-controlled backups.
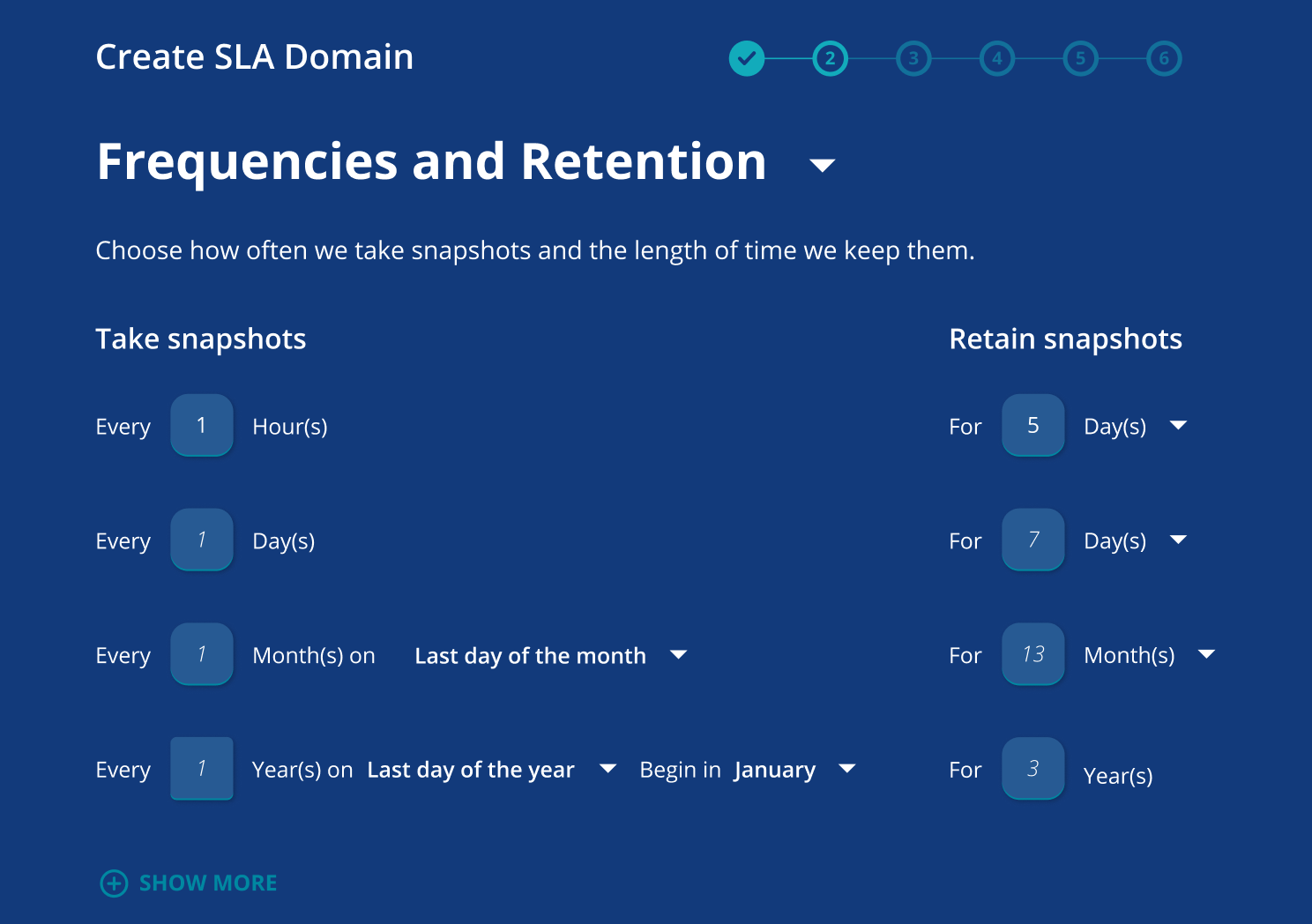
Unstructured Data Protection
Protect, monitor, and rapidly recover against cyberattacks at petabyte-scale.
Mass Recovery
Restore business operations quickly by recovering apps, files, or objects at scale.
Monitor data risk and investigate faster
Continuously monitor risks to your data, including ransomware, data destruction, and indicators of compromise.
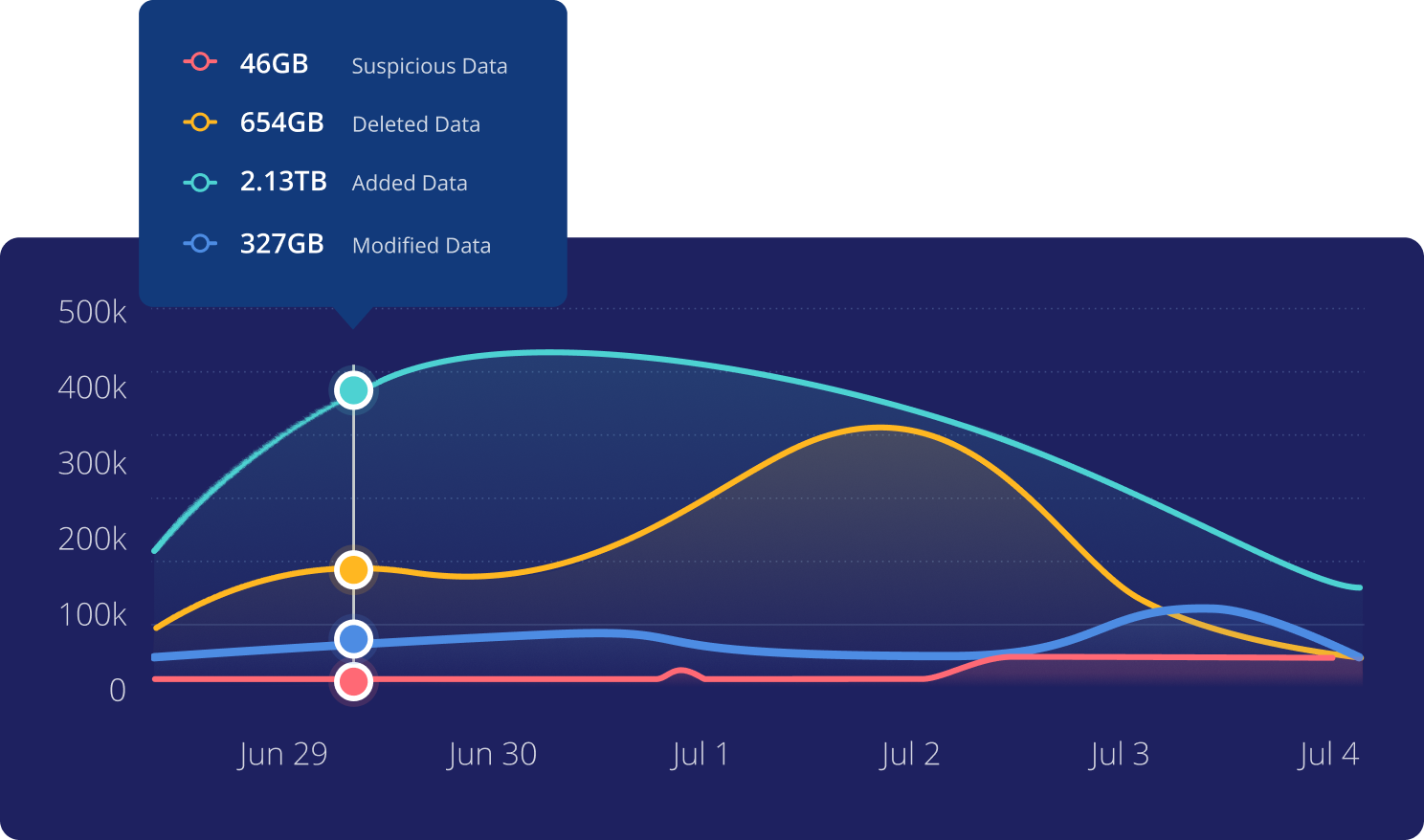
Anomaly Detection
Determine the scope of cyberattacks using machine learning to detect deletions, modifications, and encryptions.
Threat Monitoring
Detect threats early by automatically identifying indicators of compromise within backups using an up-to-date feed of threat intelligence.
Threat Hunting
Determine the initial point, scope, and time of infection by identifying specific indicators of compromise within the time-series history of backup data.
Proactively reduce data exposure risk
Identify and monitor sensitive data exposure and use intelligent risk insights to maximize data security posture.
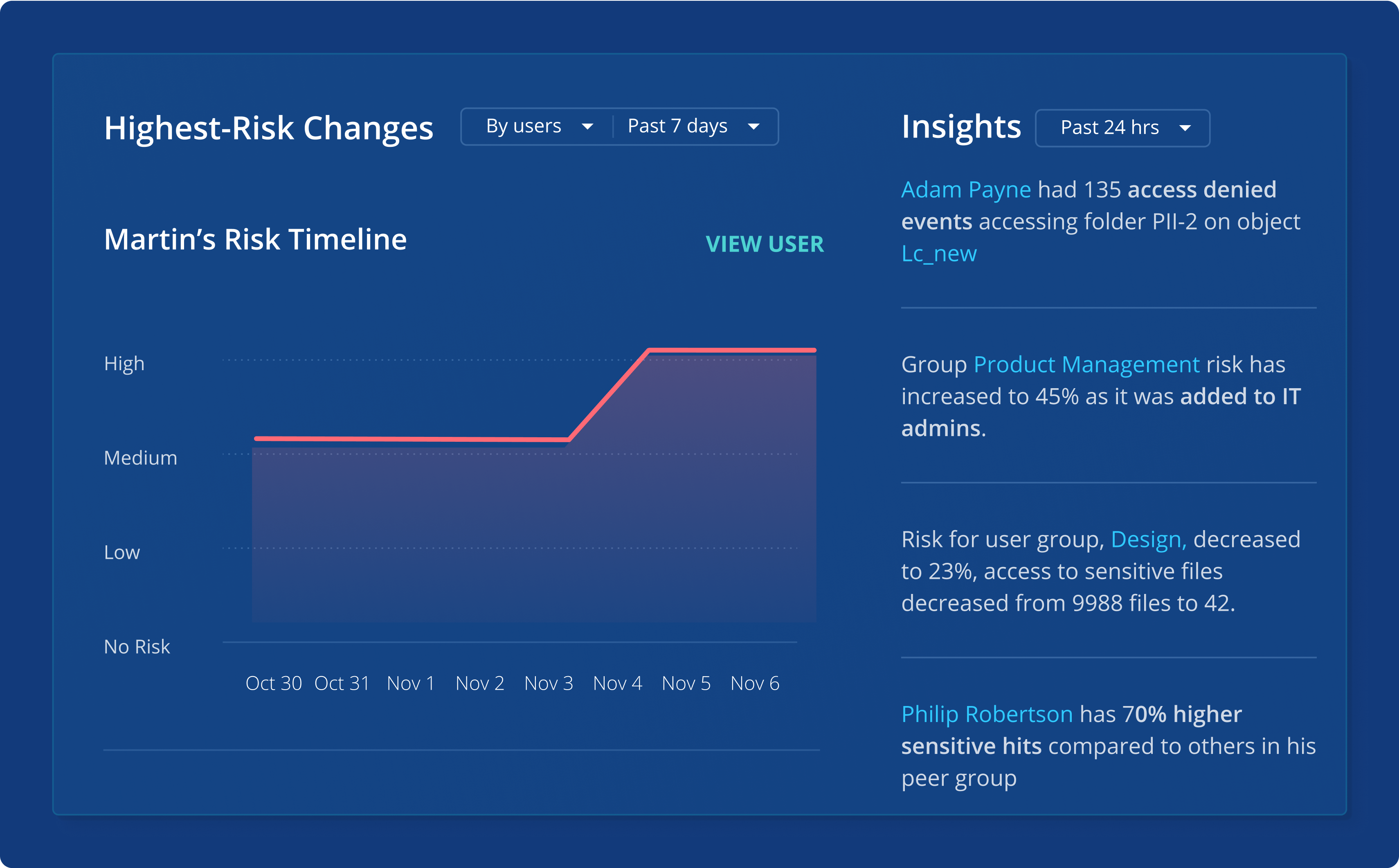
Restore business operations faster
Improve cyber readiness by easily testing and orchestrating recovery workflows while reducing the risk of reinfection.
Threat Containment
Ensure safe and quick data recovery by quarantining data infected with malware.
Cyber Recovery Simulation
Improve cyber readiness and incident response by easily creating, testing, and validating cyber recovery workflows.

Maximum Cyber Resilience. Maximum Peace of Mind.
Rubrik is confident in its data recovery. Hence, we offer our customers $10M ransomware recovery warranty.
* Terms and conditions apply. Maximum warranty available dependent on volume of data protected. Refer to warranty agreement for more information. This warranty may be subject to additional local laws and regulations in certain jurisdictions. Rubrik reserves the right to modify the terms of this warranty or refuse to offer this warranty in any jurisdiction in its sole discretion due to requirements imposed by local laws and regulations.
Protecting Hybrid and Multicloud Data
Learn how to integrate cloud platforms with on-premises infrastructure to provide a single control pane to manage, back up, and restore data across your whole environment.
Develop a Ransomware Remediation Plan
Learn how to prepare and quickly recover from a ransomware attack, and walk through every phase of your plan, from preparation to remediation.
Ready to get started?
Get a personalized demo of the Rubrik Zero Trust Data Security platform.















