Threat Monitoring
Find lurking threats early
Detect security threats early by automatically identifying indicators of compromise within backups using an up-to-date feed of threat intelligence.
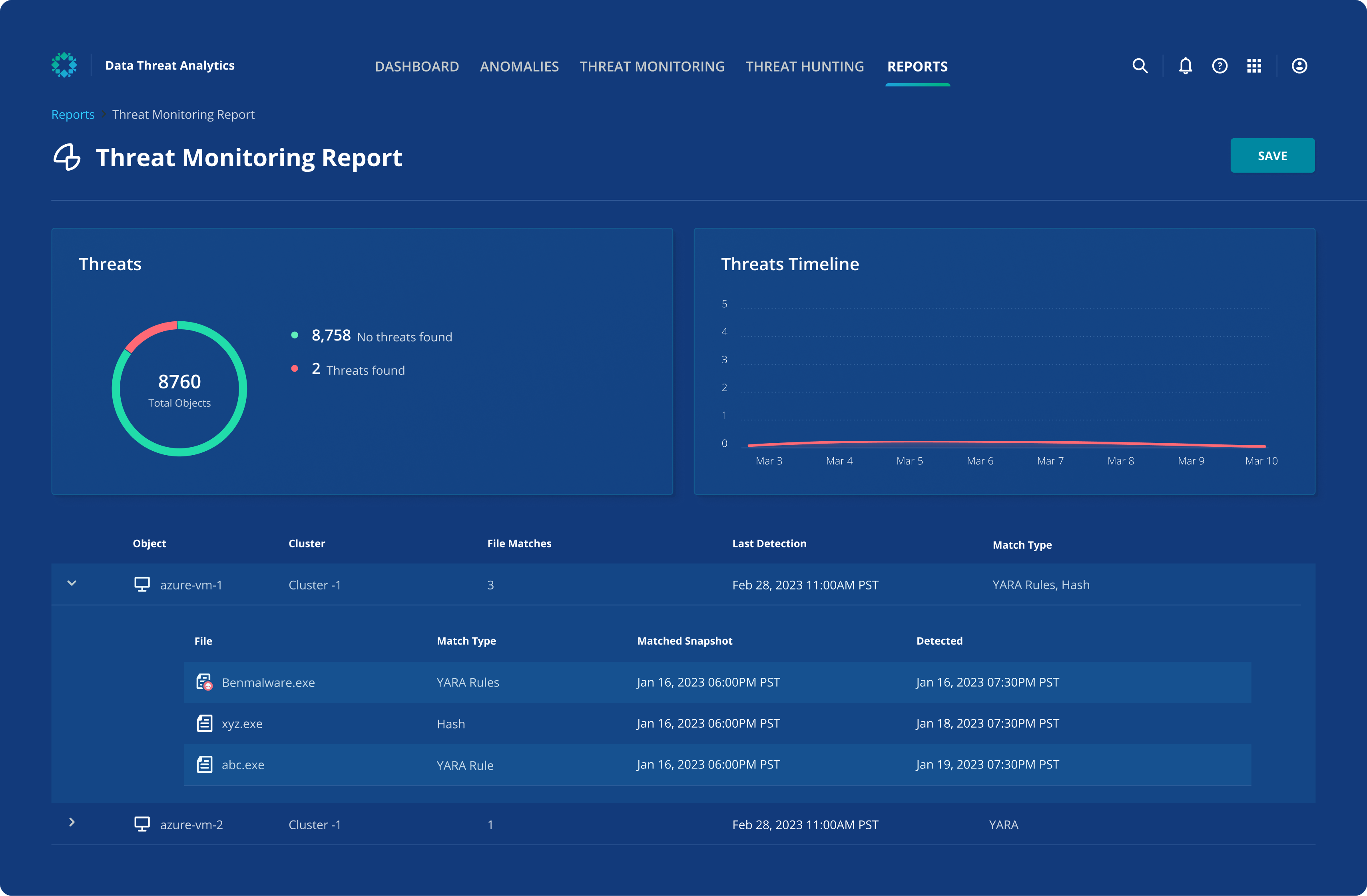
Discover threats
Identifying malware lurking in your infrastructure can be challenging. Rubrik Threat Monitoring accelerates investigations and reduces the risk of malware reinfection during recovery by automatically analyzing backup snapshots for threats using an up-to-date threat intelligence feed.
Detect Threats Early
Use Rubrik’s up-to-date threat monitoring and intelligence, based on multiple sources, to understand the latest security threats.
Monitor for Threats Automatically
Scan backups automatically for indicators of compromise using file hashes and YARA rules.
Minimize Impact to Production
Monitor existing backup data out-of-band from production.
Gartner 2024 Critical Capabilities report for Enterprise Backup and Recovery Software Solutions
Rubrik ranks #1 in the Ransomware Protection, Detection, and Recovery Use Case!

Use up-to-date threat intelligence
Automatically ingest vetted threat intelligence from Rubrik’s InfoSec team, Rubrik Zero Labs, threat intelligence programs, and third party sources.
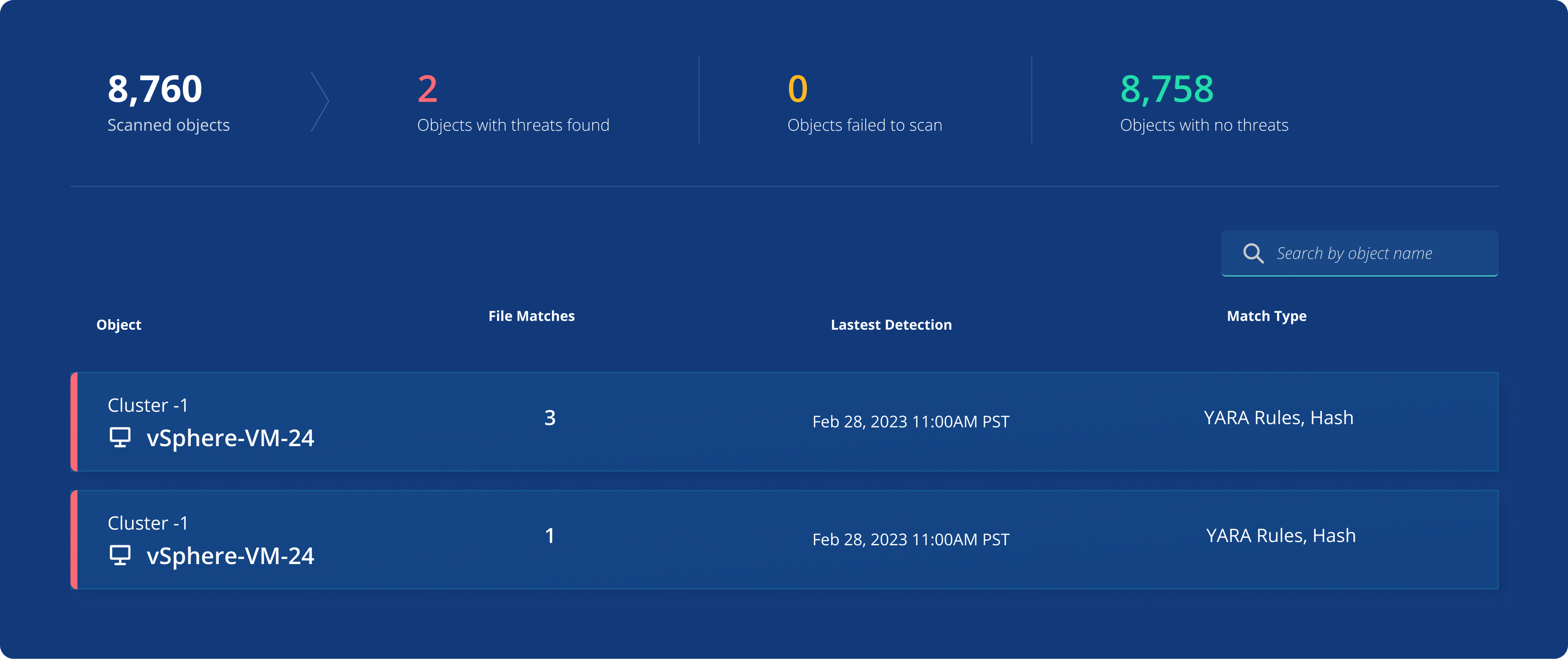
Get alerts for lurking threats
Hunt for indicators of compromise or data breach automatically based on the latest threat intelligence and monitoring solutions.
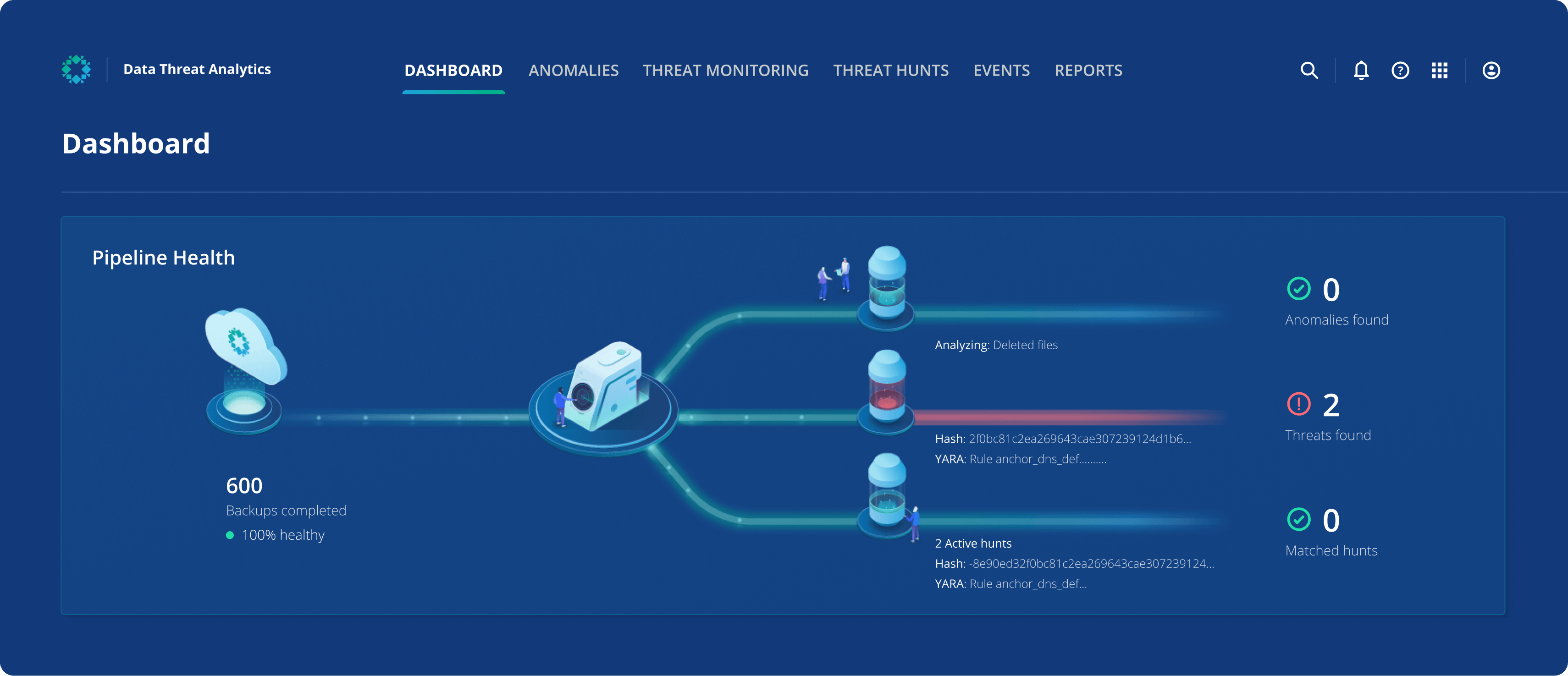
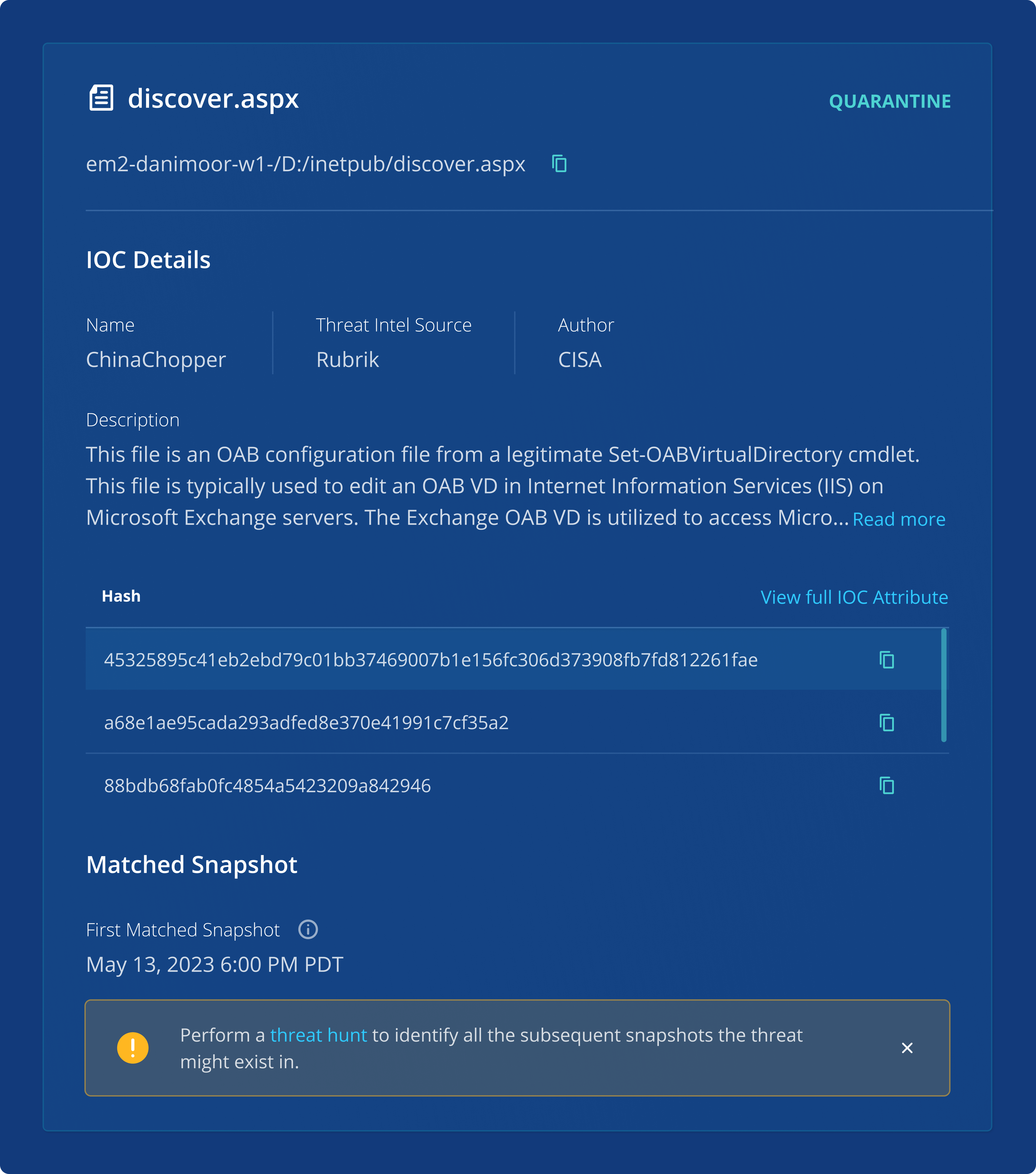
View infection insights
Leverage insights from IOC scans for deep internal and external cyber investigations into attack surfaces.
10 Tips for Preventing and Recovering from a Ransomware Attack
Discover ten tips you can use to prepare for and recover from ransomware, so you can come out the other end with your data intact.


Prepare and Recover from a Ransomware Attack
Learn best practices to plan for, identify, and remediate ransomware attacks. Quickly and effectively recover your data to minimize damage to the business.
From Reactive to Proactive: Harnessing the Power of Threat Monitoring
Threat Monitoring utilizes an up-to-date threat intelligence feed which is vetted by Rubrik’s team of experts.
Rubrik Threat Monitoring Product Tour
See how Rubrik Threat Monitoring scans your backup files and compares suspicious activity to current threat intelligence.

