overview
Completed Certifications & Attestations
At Rubrik, we understand the importance of building solutions with security, privacy and confidentiality in mind. Our products and services are regularly independently verified for compliance, security, and privacy. We have achieved certifications and attestations of compliance against global standards. Our continued investments in compliance and security are illustrated by the certifications and attestations of compliance below.
Company
Data Compliance
Data privacy and protection lies at the heart of what we do. We are committed to complying with these data privacy frameworks and regulations to keep your data safe.


The General Data Protection Regulation is a European regulation to ensure that companies who do business both within and outside the European Union protect the personal data and privacy of EU citizens by giving individuals greater control over their personal data.

The Privacy Shield Framework demonstrates a company's commitment to comply with the data protection requirements set forth by the European Union and Switzerland for personal data.

The California Consumer Privacy Act is a law regulating how companies can use, store, or otherwise handle the personal data of California residents.
Cloud Data Management
Manage & Protect Your Data in the Cloud
At Rubrik, we continue to invest in Cloud Data Management (CDM), and support these key standards and frameworks to build a strong foundation for CDM and simplify how you manage and protect data in the cloud.
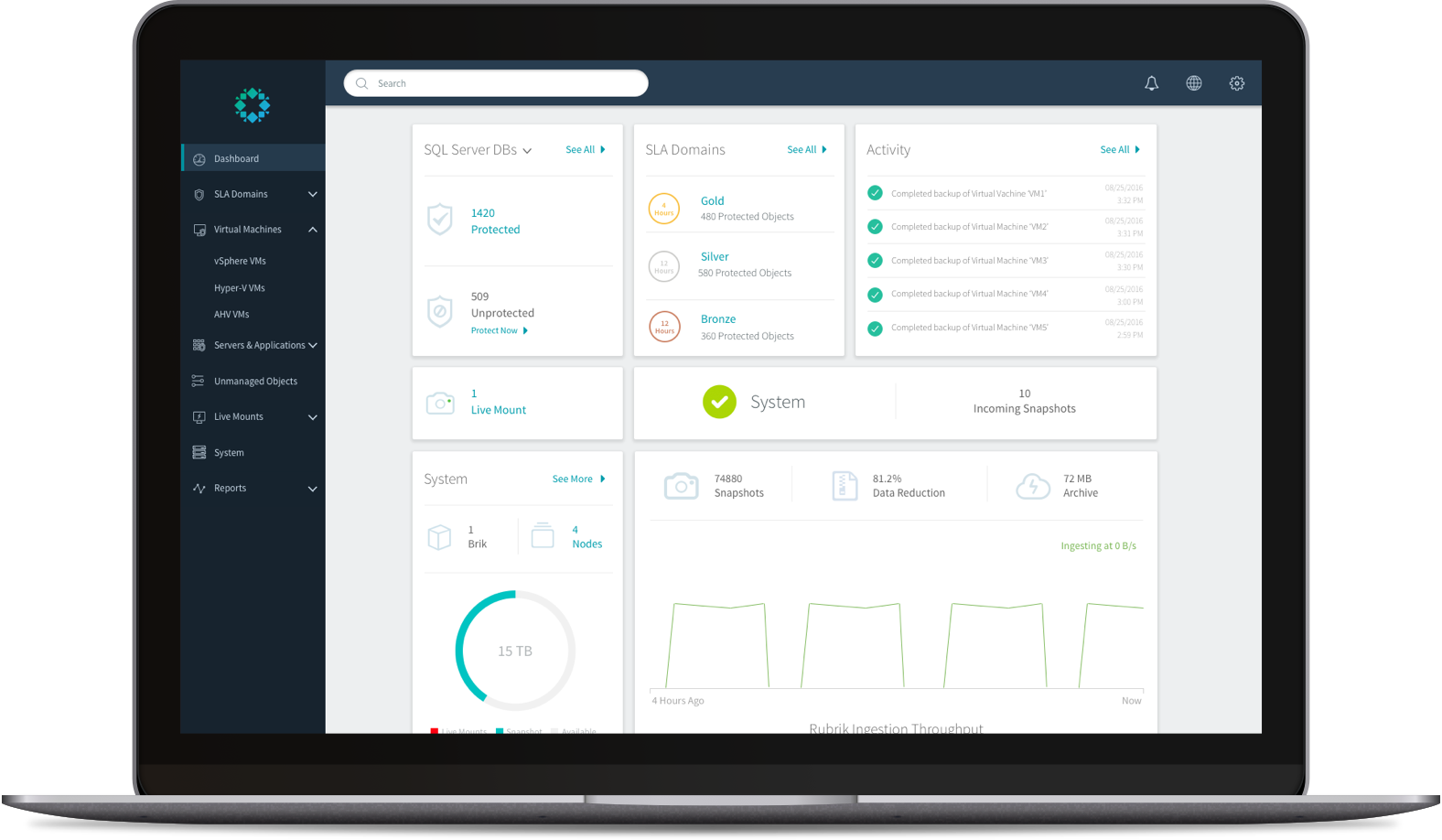
CDM Products and Support Services

The Department of Defense Information Network (DoDIN) Approved Product List (APL) provides a consolidated list of products that are approved for purchase by the U.S. Department of Defense (DOD).

FIPS 140-2 is a government computer security standard used to approve cryptographic modules for use in government departments and regulated industries.

Common Criteria is an internationally recognized set of guidelines that define a framework for evaluating security features and capabilities of IT security products.

ISO 27001 is an internationally recognized information security standard that provides the requirements for an information security management system (ISMS), outlines best practices, and details security controls to help manage information risks.

SOC 2 reports on the controls at a service organization relevant to Security, Availability, Processing Integrity, Confidentiality or Privacy. At Rubrik, we are SOC 2 Type II certified against the security, confidentiality and availability criteria.

SOC 3 reports evaluate the same criteria as SOC 2. Unlike SOC 2, these are publicly available general use documents.
Rubrik Polaris
Data Management Applications
By investing in and achieving the compliance certifications and standards below for Rubrik’s Polaris SaaS platform and services, we are laying out the foundation for a stronger platform, products, and services.
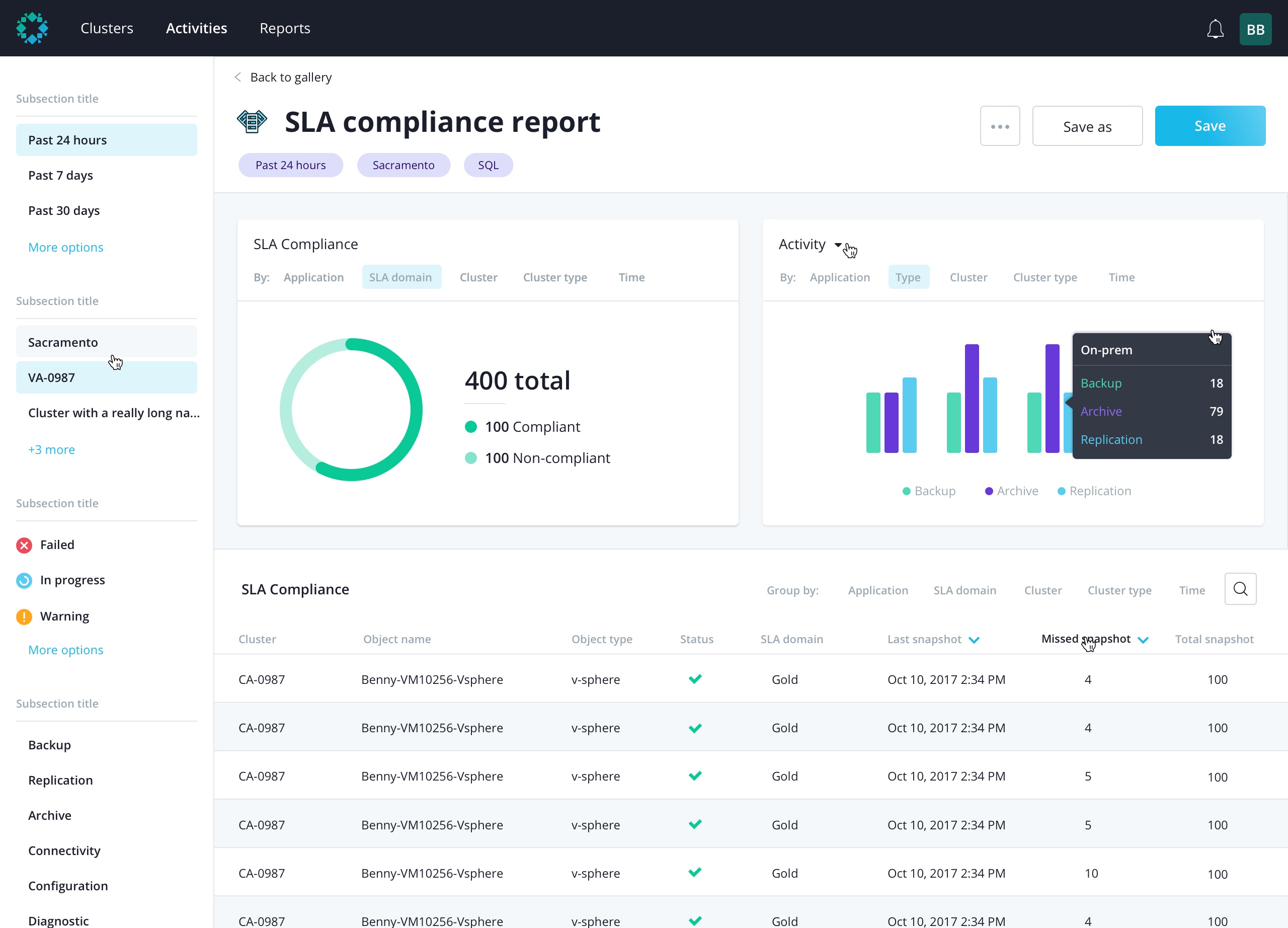
Polaris Products and Support Services

ISO 27001 is an internationally recognized information security standard that provides the requirements for an information security management system (ISMS), outlines best practices, and details security controls to help manage information risks.

ISO 27017 provides guidelines supporting the implementation of information security controls for cloud service customers and cloud service providers based on the ISO 27002 standard.

ISO 27018 is a reference for selecting personally identifiable information (PII) protection controls when implementing a cloud computing information security management system based on ISO 27001, or as guidance for implementing commonly accepted PII protection controls for organizations acting as public cloud PII processors based on the ISO 27002 standard.

SOC 2 reports on the controls at a service organization relevant to Security, Availability, Processing Integrity, Confidentiality or Privacy. At Rubrik, we are SOC 2 Type II certified against the security, confidentiality and availability criteria.

SOC 3 reports evaluate the same criteria as SOC 2. Unlike SOC 2, these are publicly available general use documents.
Learn more