vm workloads
Data Security for Virtual Environments
Cyber-proof your VMs against ransomware and other cyber threats. Simplify data protection and management, and accelerate VM recovery.
Protect Virtual Environments from Cyber Threats
Reduce data risks, simplify data protection and accelerate clean recovery for virtual environments.
Protect Against Ransomware
Simplify Data Protection
Accelerate recovery
Utilize global, real-time predictive search to quickly find VMs, apps and files. Leverage simple, quick recovery options for near-zero RTOs. Rapidly recover your VMs while avoiding malware reinfection.
Prepare and Recover from Ransomware with Rubrik
This guide explains Rubrik Zero Trust Data Security and how its built-in capabilities make protected data immune to ransomware. You'll also learn about deployment best practices that make it even tougher for cybercriminals to attack.

Replace your manual scripting and job scheduling
Automatically discover and protect your virtual environments across on-premises and the cloud, regardless of their deployment configurations.
Automate VM Discovery
Rubrik automatically discovers details of your entire virtual environment using natively integrated APIs.
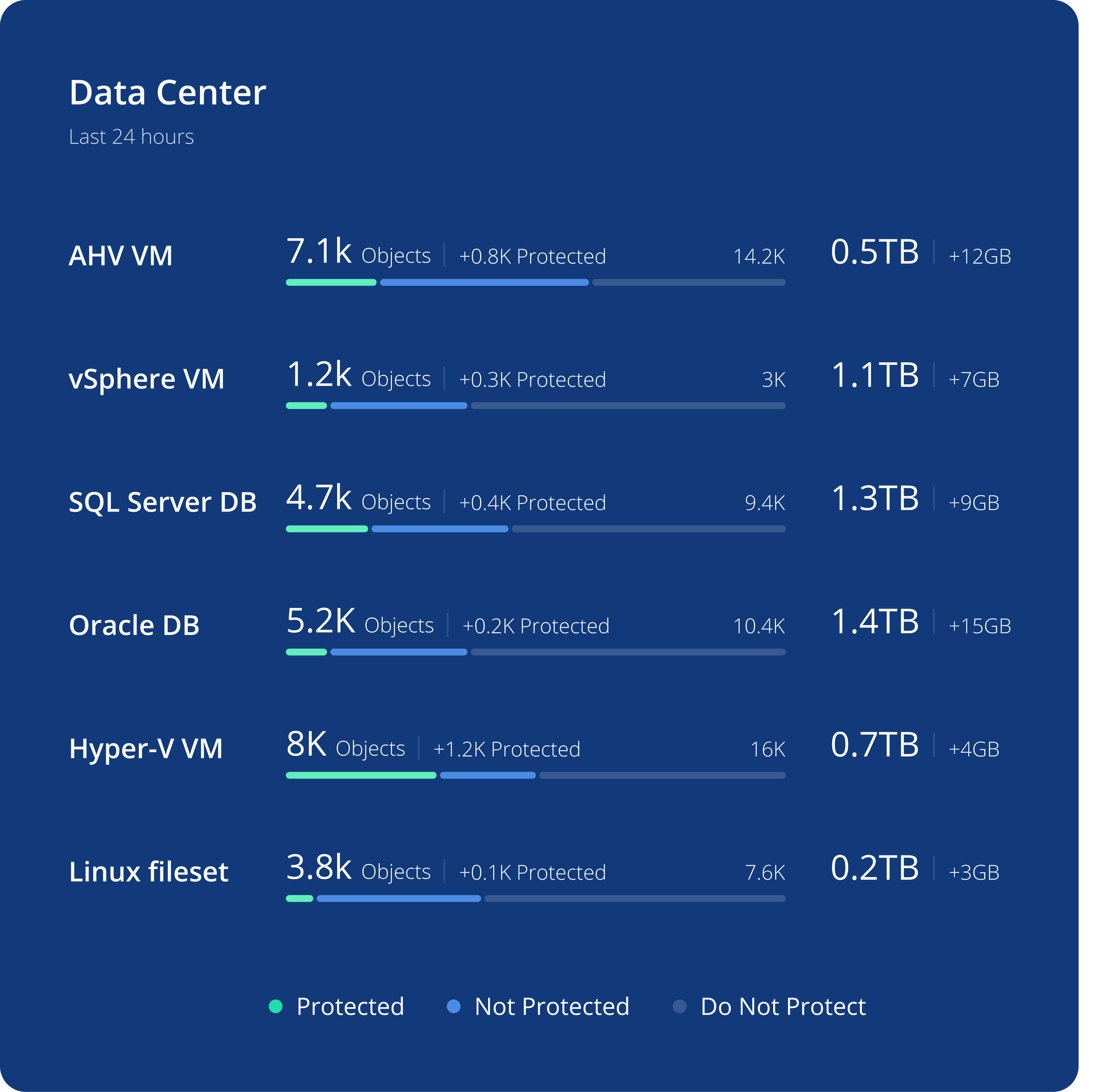
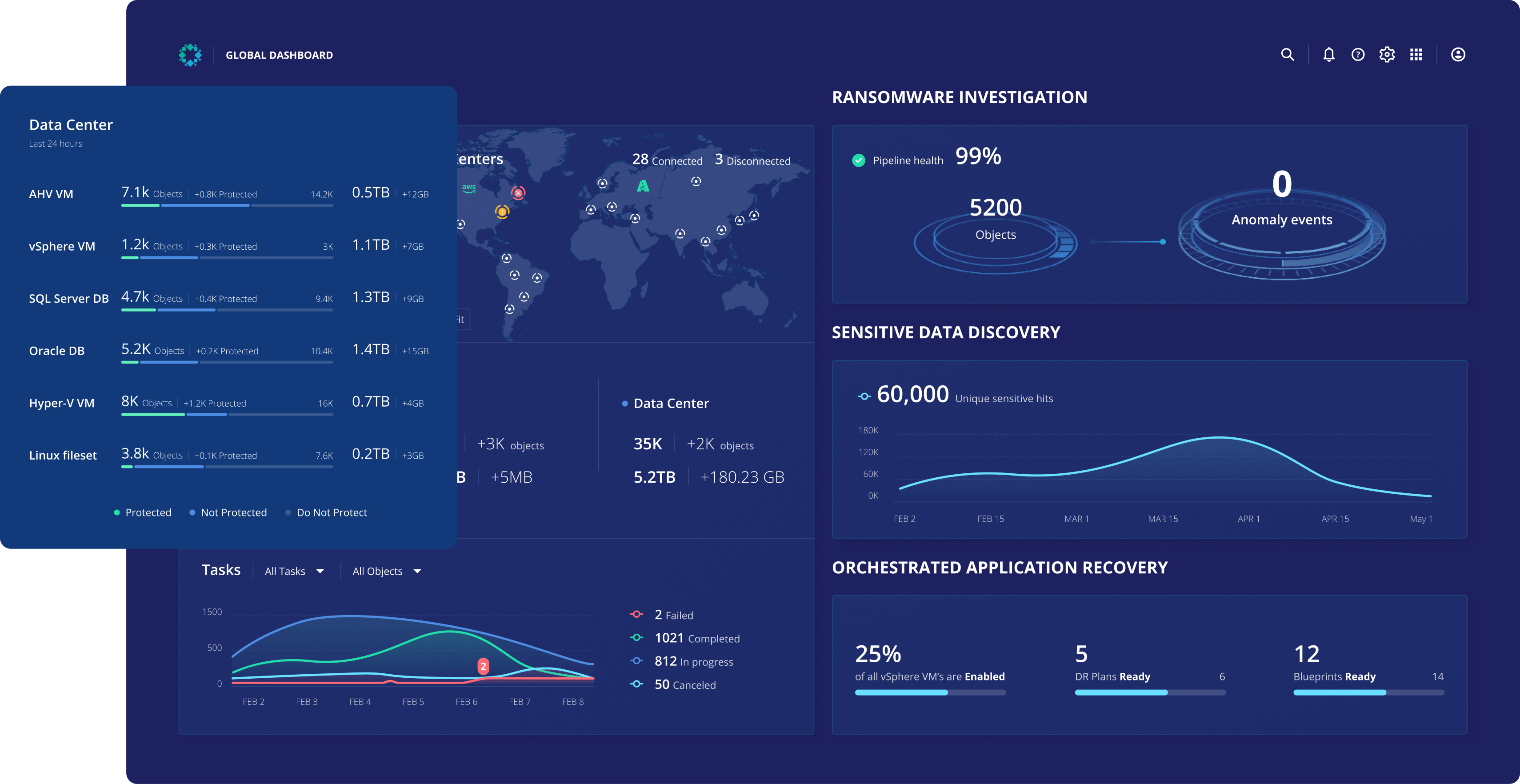
Simplify Data Protection
Protect your VMware data from cyber-attacks with an air-gapped, immutable file system that can’t be modified, deleted, or encrypted by hackers. Declare SLA automation policies at the cluster, host, or folder levels and never worry about leaving a VM unprotected again.
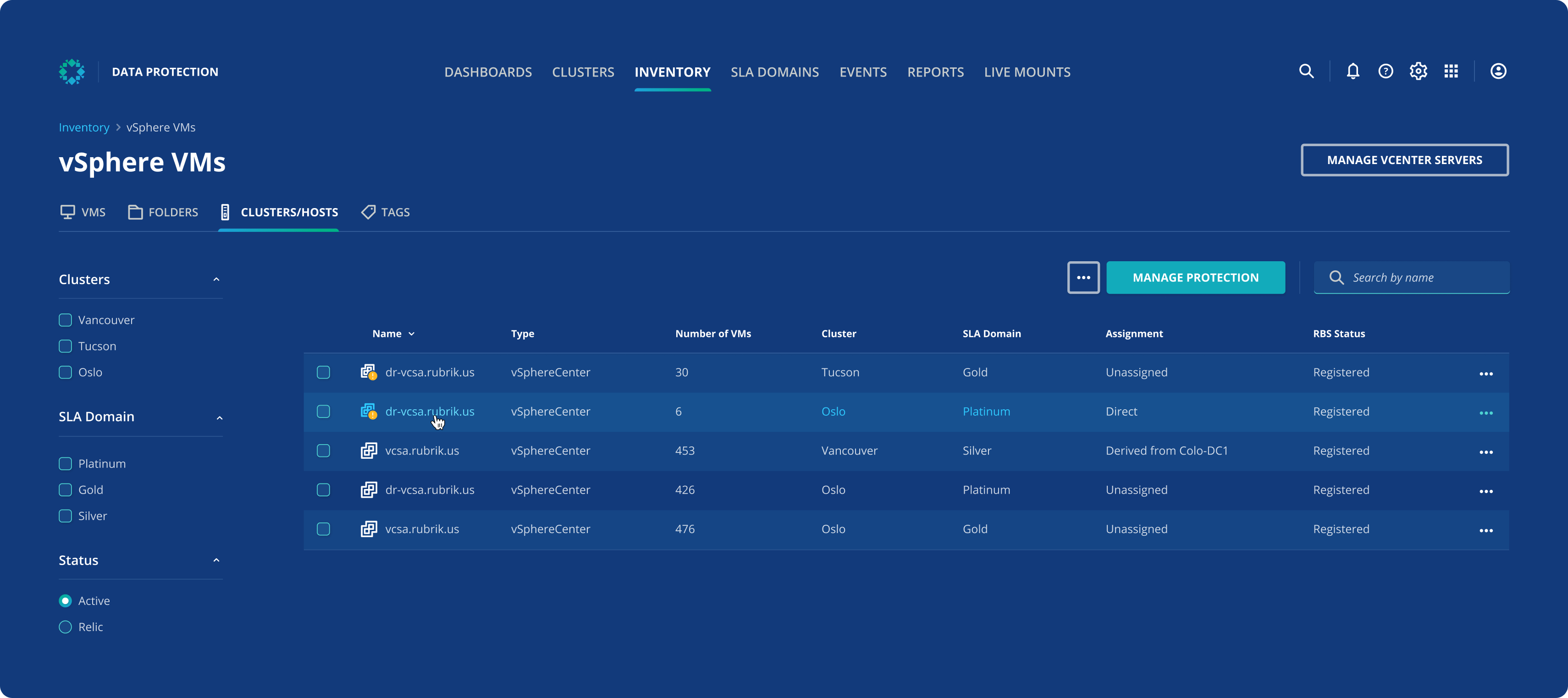
Operationalize Backups
Leverage Rubrik Live Mount and our powerful APIs to simplify your day to day. From automation, to migration, and self-service clone creation, the sky’s the limit.
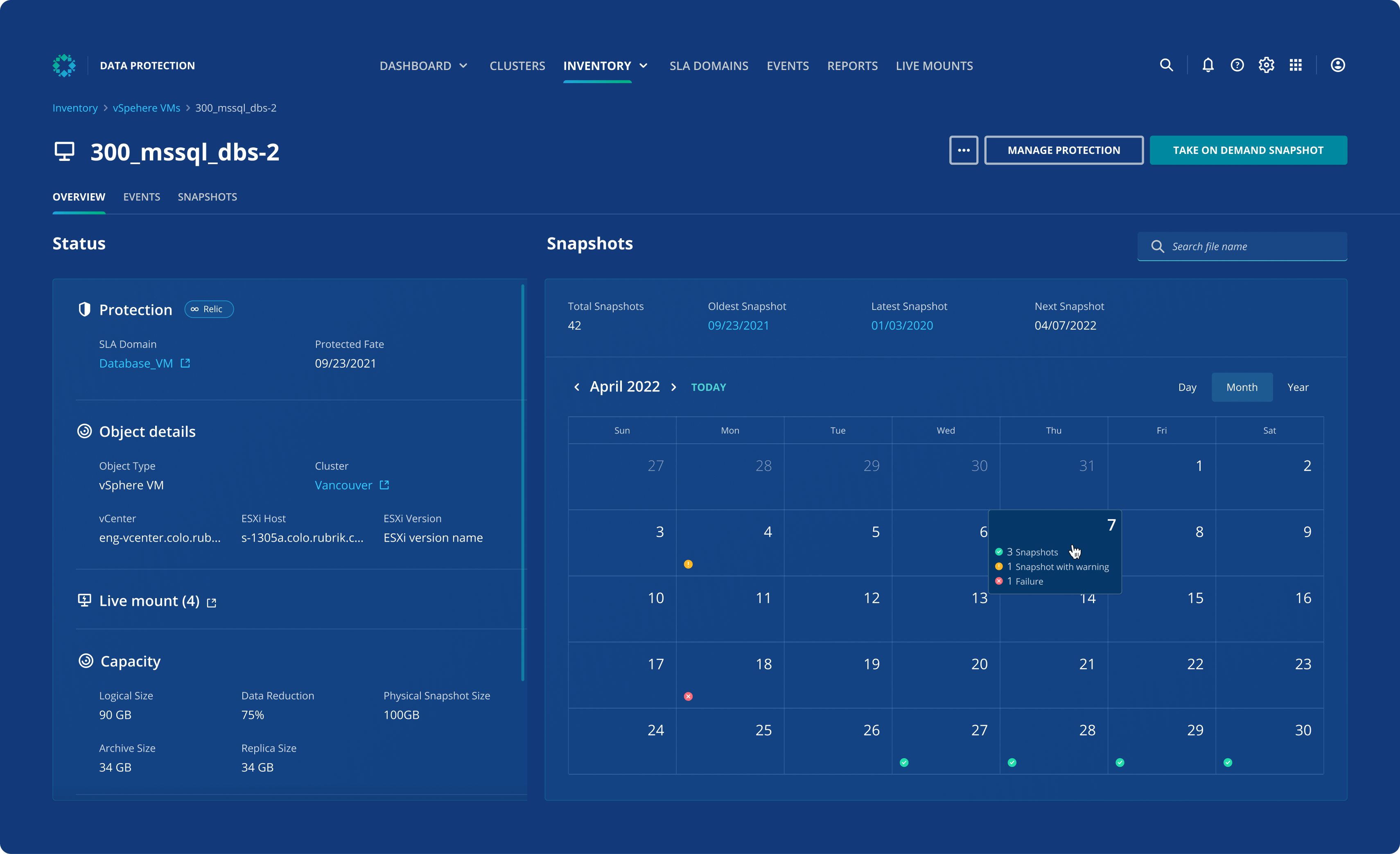
Gain peace of mind with Rubrik’s data security features
Continuously monitor and remediate data risks, including ransomware investigation, sensitive data discovery, and threat hunting.
Ransomware Monitoring & Investigation
Determine the scope of ransomware attacks, using high fidelity machine learning to detect deletion, modifications, and encryptions.
Sensitive Data Monitoring & Management
Reduce sensitive data exposure by discovering what types of sensitive data you have, where it lives, and who has access to it.
Threat Monitoring & Hunting
Prevent malware reinfection by analyzing the time-series history of data for indicators of compromise to identify initial point, scope, and time of infection.
Data Security Command Center
Identify security gaps, categorize data risks and get actionable guidance to improve your overall data security.
Drive recovery times down to minutes
Surgically and rapidly recover your VMs and files while avoiding malware reinfection.
Search Anything
Search for VMs and files with global real-time search, on-prem to cloud. Locate specific versions of files across a multi-hypervisor, multi-cloud environment.
Reduce Recovery Risk
Ensure safe and quick data recovery by quarantining data infected with malware thereby preventing reintroduction of malware that disrupts business operations.
Mass Recovery
Recover hundreds of VMs—in bulk, or restore tens of thousands of files to a clean state, within minutes.
Definitive Guide to Zero Trust Data Security
Cyber threats are growing at an alarming rate. Learn how to protect backup data and minimize the impact of ransomware attacks with Zero Trust Data Security.

VMware
Rubrik delivers business resilience against cyber attacks, simplifies data protection and accelerates recovery for enterprises running on VMware vSphere, VMware Cloud Foundation, vSAN, vRealize suite and Cloud Director environments.

Nutanix
Rubrik delivers zero trust data security for Nutanix environments across multiple hypervisors (AHV, ESXi, and Hyper-V), file servers, including Nutanix Files, and public and private cloud storage tiers with support for Nutanix Objects, AWS, Azure, Google Cloud Platform, and Oracle Cloud.

Hyper-V
Rubrik provides zero trust data security for virtual machines that are deployed in a Microsoft Hyper-V environment. Automate data protection by applying SLA policies anywhere in the hierarchy stack - SCVMM, the cluster, Hyper-V host, or virtual machines.

Rubrik For Microsoft Hyper-V and Azure Stack HCI
Deliver complete data security for your Hyper-V and Azure Stack HCI environments.
Rubrik Security Cloud for Nutanix
Complete cyber resilience delivered for your Nutanix environments.
Rubrik and Nutanix Extend Partnership to Enhance Security for Nutanix Cloud Clusters (NC2) on AWS and Azure
Cyber threats pose a significant risk to virtualized infrastructure. According to the latest Rubrik Zero Labs report, 83% of encrypted data across all industries is within a virtualized architecture.
VM Encryption Detection
Join this hands-on lab to see how Rubrik Anomaly Detection can monitor virtual machines and notify you if a VM has suffered an encryption attack.
