Ransomware Recovery
Accelerate Ransomware Recovery
Our backups can't be encrypted or deleted during a ransomware attack, enabling customers to recover quickly to the most recent clean state with added intelligence on attack impact.
Avoid Paying Costly Ransoms
Organizations are destined to pay a ransom if they can’t recover encrypted files quickly – not to mention experience significant revenue and brand damage. When an attack occurs, Rubrik provides visibility into the scope of damage, fast restore from uncompromised backups of important files for business continuity, and alerts that uncover unusual behavior from the ransomware infection.
Instant Ransomware Recovery
Ransomware-Immune Backups
Our file system was built from scratch to be immutable. That means backups can't be encrypted or deleted by a ransomware attack.
Impact Analysis
Ransomware Recovery for Dummies
Learn how to build a recovery plan that makes sense and keeps your organization safe.

Secure Architecture
Advanced ransomware attacks are now targeting backups – modifying or completely wiping them out. Rubrik stores all data in an immutable format, meaning ransomware cannot access or infect your backups. Additional security measures include multi-factor user authentication, zero-trust cluster design, and retention lock support.
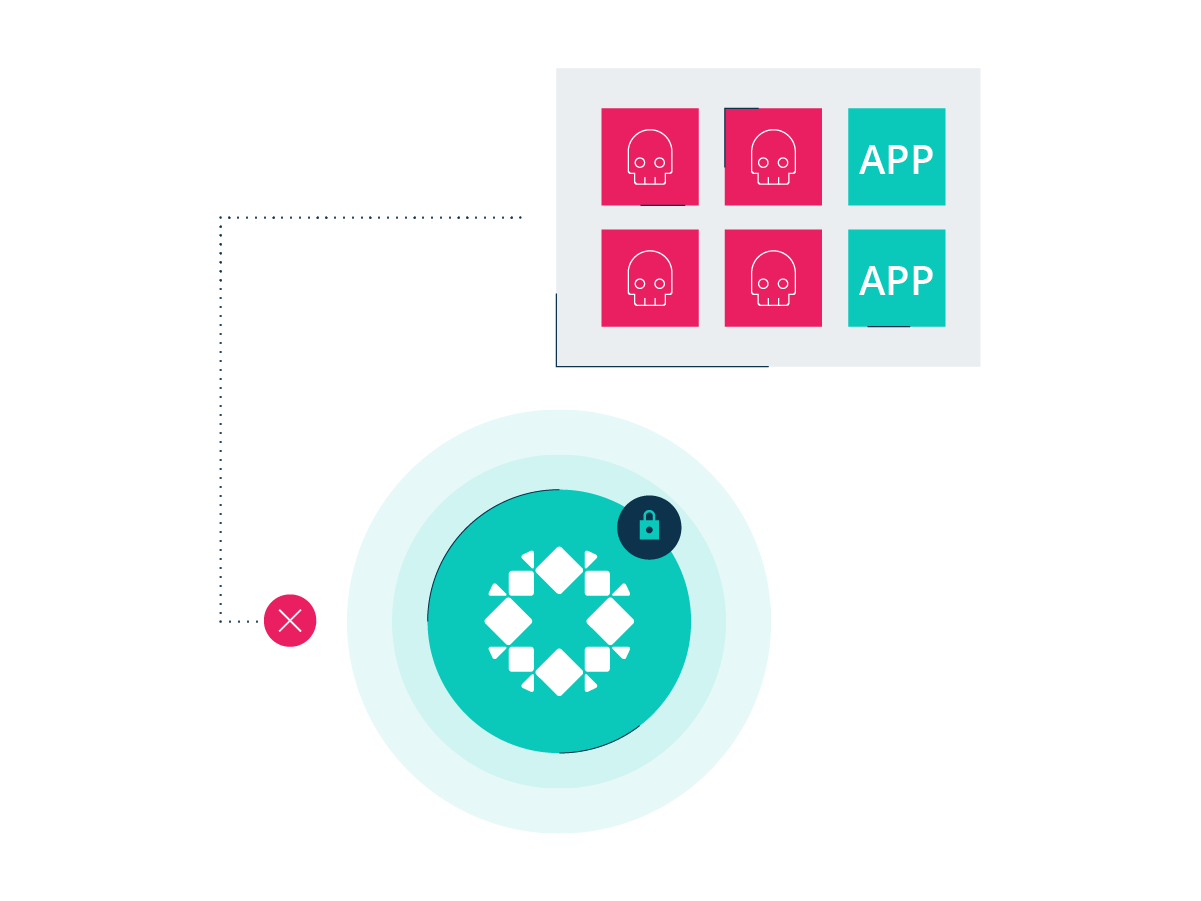
Anomaly Detection
Ransomware Investigation proactively analyzes behavioral patterns and flags any unusual activity as your last line of defense. All without impact on your production systems.
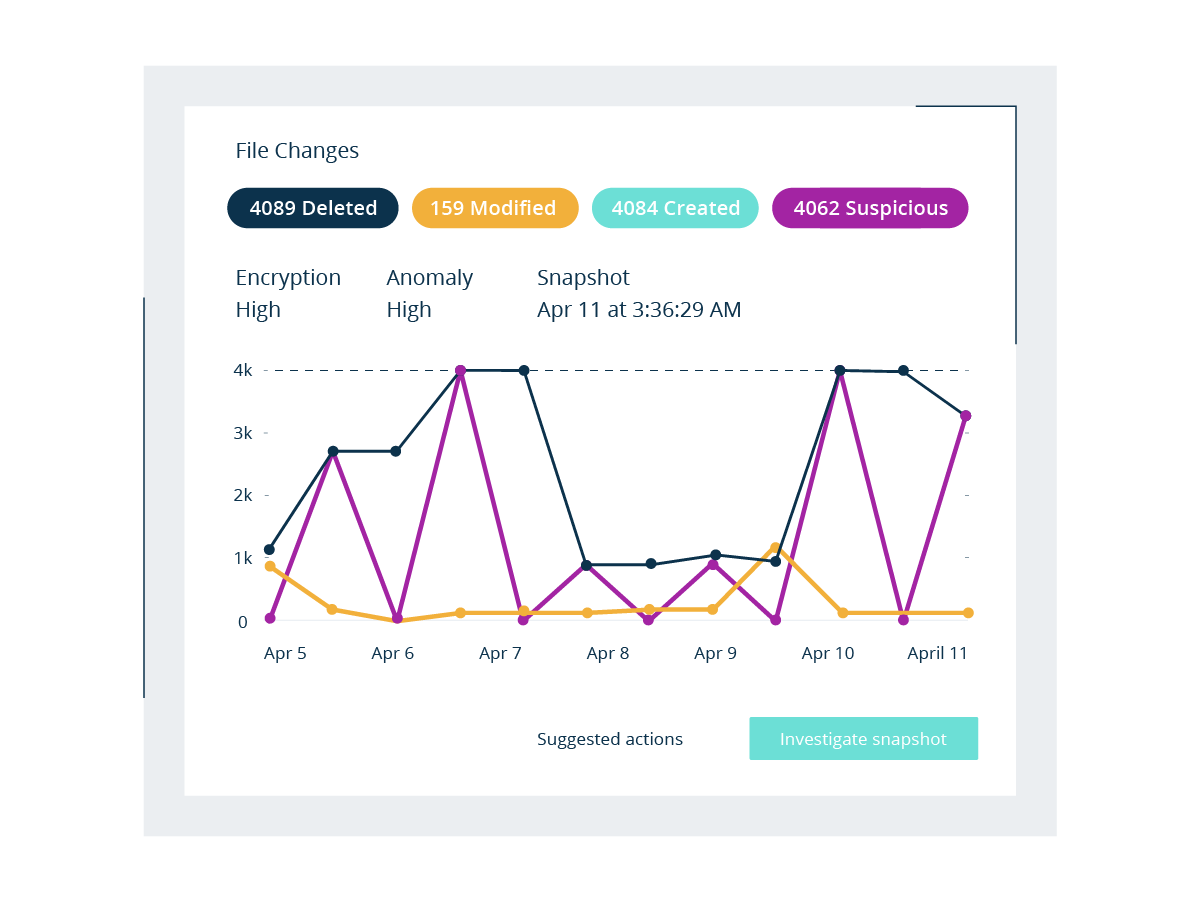
Accelerated Ransomware Recovery
Quickly restore to the most recent clean version of your data, whether you need to do a full, orchestrated recovery or partial system restore. Integrate Rubrik into popular SIEM, SOAR, Syslog, or security automation frameworks using our APIs for automated recoveries and enriched intelligence.
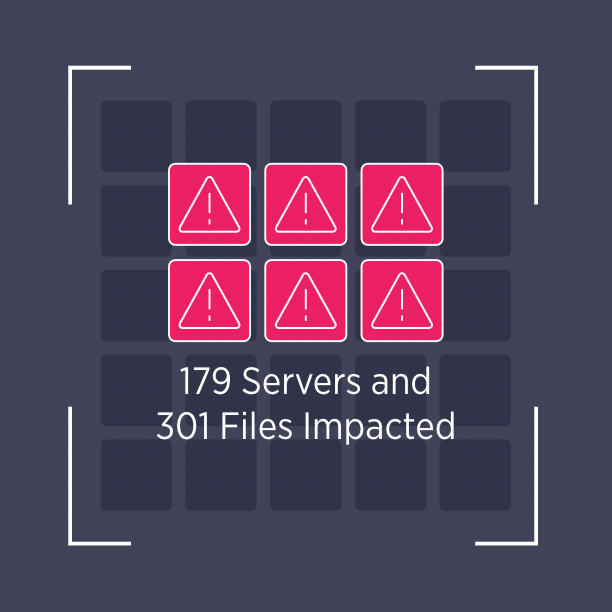
Scope of Damage Diagnosis
After an attack, Rubrik automatically diagnoses the scope of the ransomware attack, providing a clear view into what data was affected and where it resides. With modern ransomware threatening to publicly disclose stolen data, you can now identify if certain personally identifiable information (PII) or protected health information (PHI) may have been exposed by cybercriminals.
Your A-Z guide for building your cyber recovery playbook
The better prepared you are for an attack, the better your chances of bouncing back. Here’s everything you need to build your ideal cyber recovery playbook.
Ransomware Recovery Products
CDM
Sensitive Data Discovery
Ready to get started?
Get a personalized demo of the Rubrik Zero Trust Data Security platform.