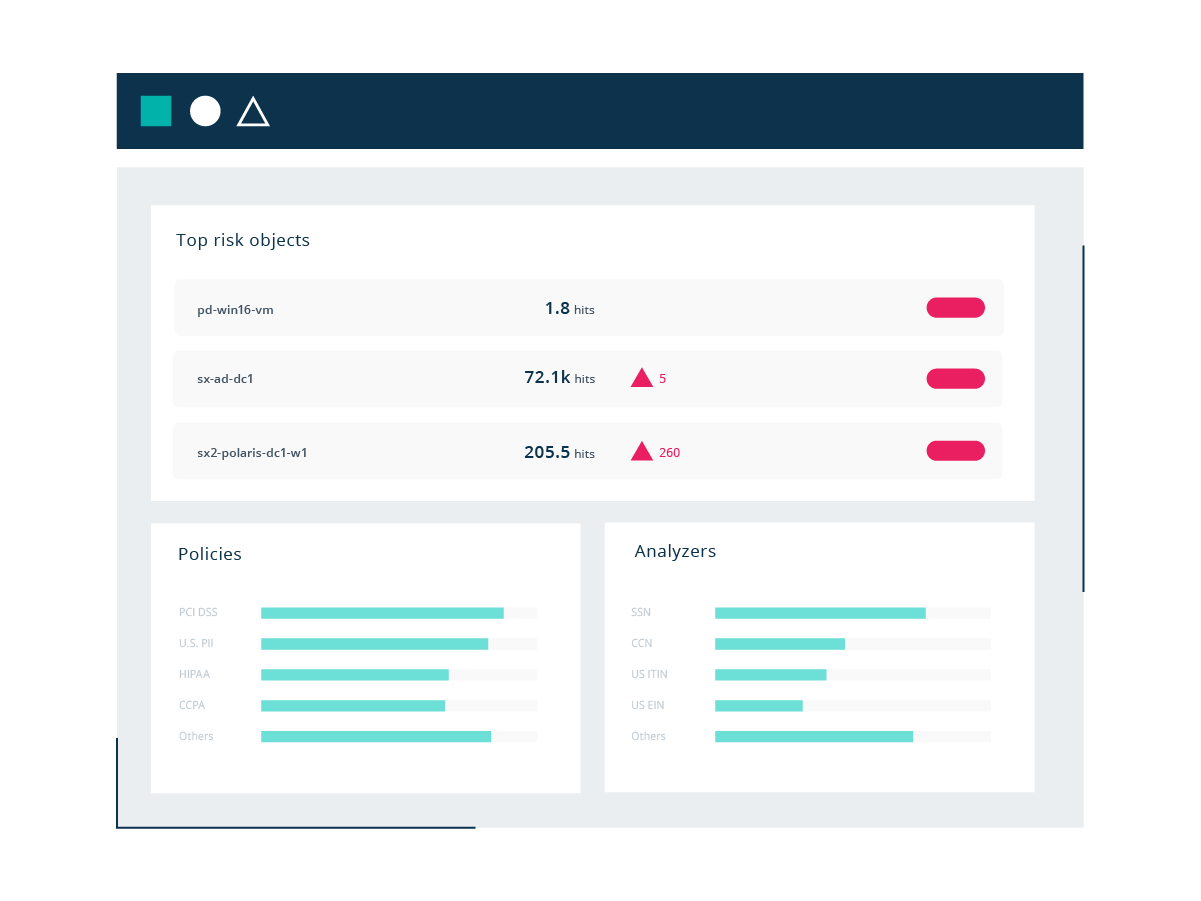
Stronger Data Governance
The costs of a data breach and non-compliance with data privacy regulations are increasing. With the surge in data, it’s hard to track at-risk data. Often, this is a time-consuming, manual process. Sonar can automate discovery of certain personally identifiable information (PII) and regulated data hiding in your unstructured data.
Accelerate Compliance
Implement Access Controls
Minimize Data Exposure
Instant Baseline
Leverage predefined policy templates as a starting point or create your own to identify common data types from regulations and standards such as GDPR, PCI-DSS, HIPAA, and GLBA. Sonar quickly classifies new and modified data without impact to production.

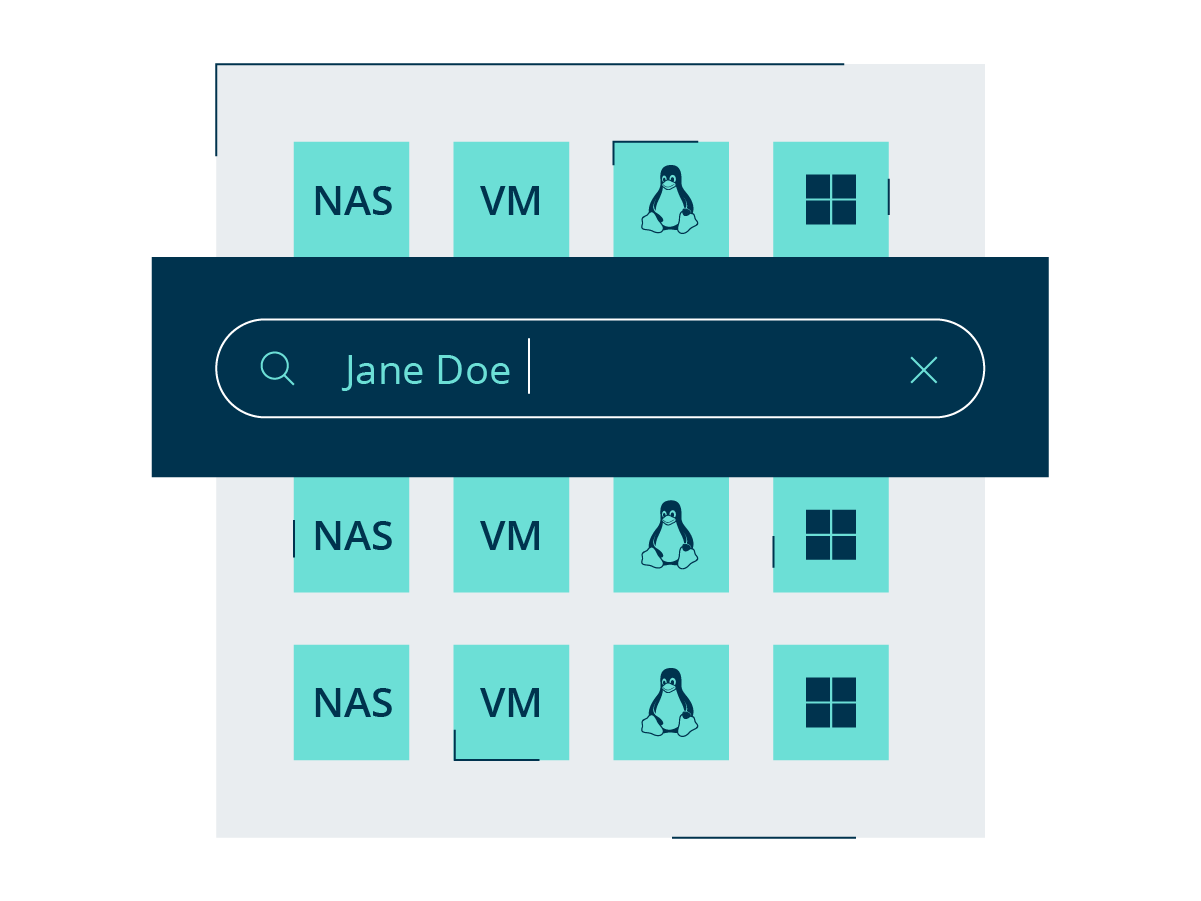
Automated Search
Search for information by keywords or custom patterns, such as name, social security number, or credit card number, across hundreds of objects via on-demand search to comply with GDPR's Right to be Forgotten, Subject Access Requests, on-demand audits, or security investigations.
Compliance Tracking
Automatically receive alerts on policy violations. Drill-down to a folder or file for granular insights. Allow list locations where sensitive information is allowed to minimize false alerts. Schedule periodic reports to share with executive leadership.